Knowledge questions: How does memory help us know? What are the limitations of our memories? Do Now: Respond to the following

A Curious Odyssey: Edwards, Roy E., Edwards, J A, Australia, Digital Print: 9781543111675: Amazon.com: Books

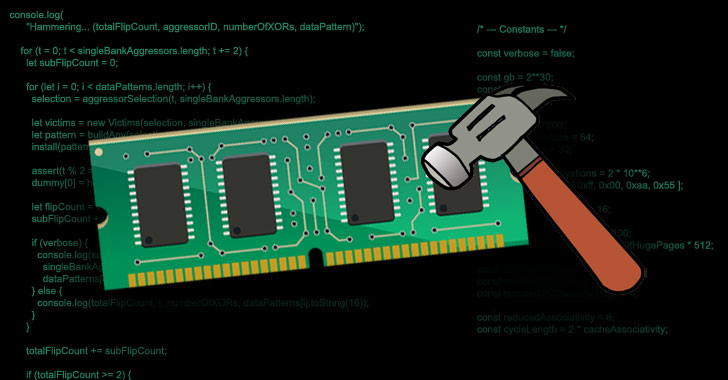
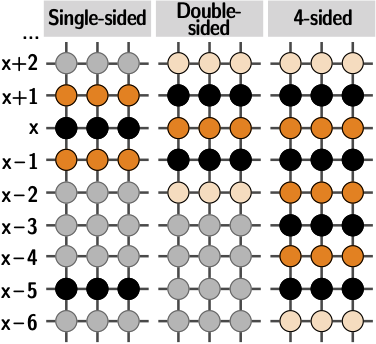
Prevent and detect software supply chain attacks | Cybersecurity & Technology News | Secure Futures | Kaspersky
![Amazon.com: The Lost Continent (1968) [Blu-ray] : Eric Porter, Hildegard Knef, Suzanna Leigh, Tony Beckley, Nigel Stock, Michael Carreras, Leslie Norman, Michael Carreras, Michael Carreras: Movies & TV Amazon.com: The Lost Continent (1968) [Blu-ray] : Eric Porter, Hildegard Knef, Suzanna Leigh, Tony Beckley, Nigel Stock, Michael Carreras, Leslie Norman, Michael Carreras, Michael Carreras: Movies & TV](https://images-na.ssl-images-amazon.com/images/I/81SmHs1SfpL._AC_UL900_SR615,900_.jpg)
Amazon.com: The Lost Continent (1968) [Blu-ray] : Eric Porter, Hildegard Knef, Suzanna Leigh, Tony Beckley, Nigel Stock, Michael Carreras, Leslie Norman, Michael Carreras, Michael Carreras: Movies & TV