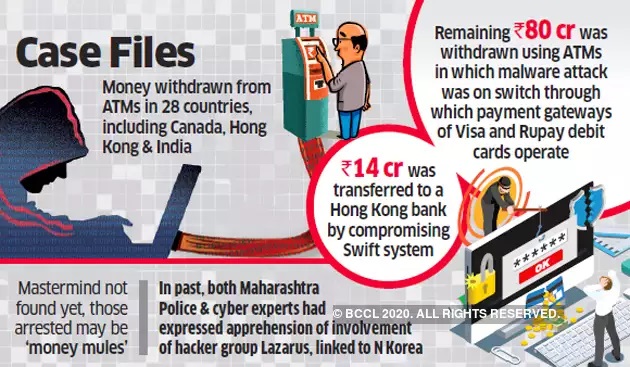
Major spike in cyber security threats: Over 6.7 lakh cases reported till June 2022, here's what Centre said
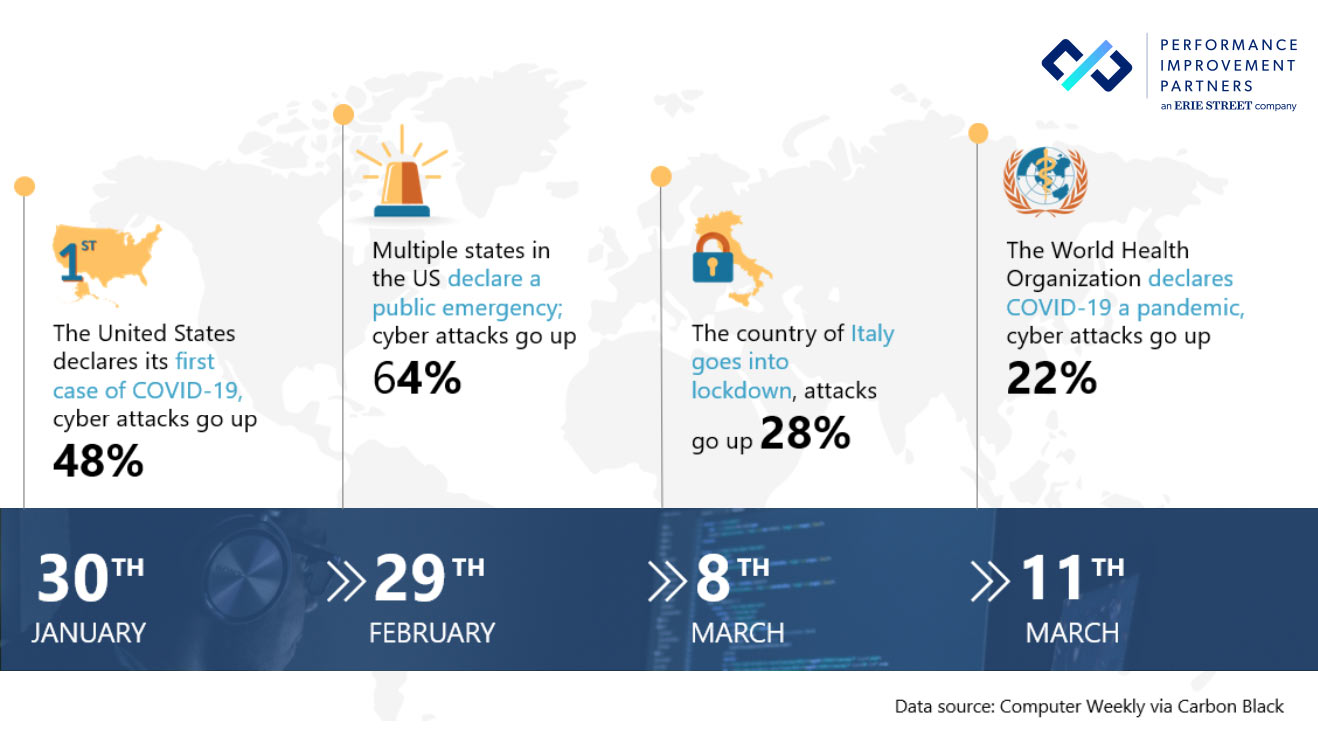
COVID-19 Cyber Security Statistics: 40 Stats and Facts You Can't Ignore - Performance Improvement Partners
Cyber Attack Case Study Ppt Powerpoint Presentation Visuals | Presentation Graphics | Presentation PowerPoint Example | Slide Templates
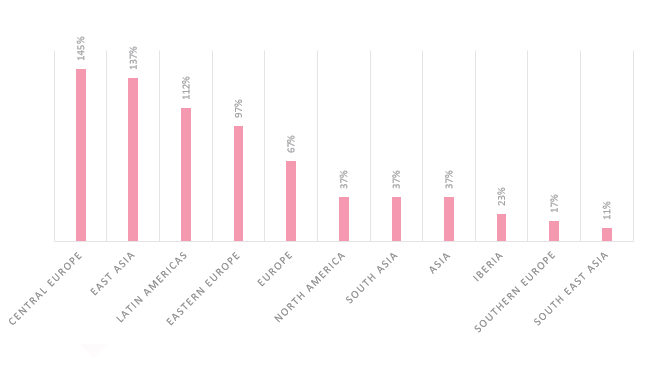
Attacks targeting healthcare organizations spike globally as COVID-19 cases rise again - Check Point Software

Cyber Case Study: SolarWinds Supply Chain Cyberattack - Ollis/Akers/Arney Insurance & Business Advisors

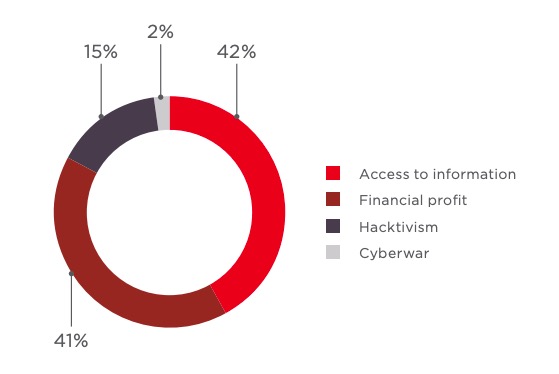
Interim report: Top Cyber Threats - smarter targeted attacks, mobile threats, and social media identity thefts by cyber-criminals using Cloud services. — ENISA

A coordinated nation-state cyber attack is a worst-case scenario, says former U.S. chief technology officer